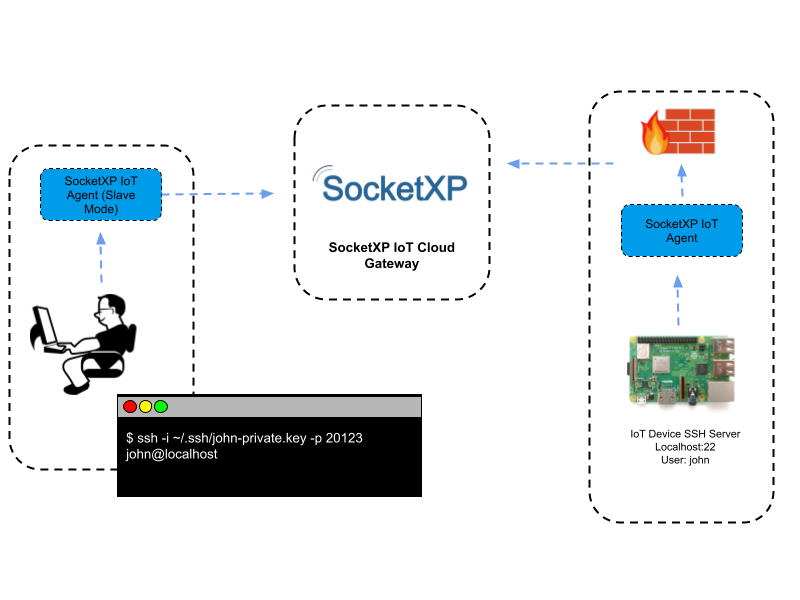
Connecting IoT devices remotely while ensuring security and bypassing firewalls has become a necessity in today's interconnected world. Whether you're a tech enthusiast, a small business owner, or an enterprise IT professional, the ability to remotely connect IoT devices behind a firewall on a Mac without relying on Windows is increasingly critical. This process involves a blend of advanced networking techniques, secure protocols, and clever workarounds that ensure seamless device management. The growing demand for remote IoT connectivity stems from the need to monitor, manage, and troubleshoot IoT devices from anywhere in the world, all while maintaining robust security measures. From home automation systems to industrial IoT applications, the ability to remotely connect IoT devices behind a firewall on a Mac is transforming the way we interact with technology.
However, achieving this level of connectivity is not without its challenges. Firewalls, by design, block unauthorized access to internal networks, making it difficult to establish a secure connection from outside the network. Additionally, the absence of Windows in the equation adds another layer of complexity, as many traditional remote access tools are built with Windows in mind. This article aims to demystify the process by providing a comprehensive guide on how to achieve a secure remote connect IoT behind firewall on a Mac without Windows. We'll cover everything from understanding the basics of IoT and firewalls to implementing advanced techniques that ensure both security and functionality.
Whether you're a seasoned IT professional or a beginner exploring the world of IoT, this article will equip you with the knowledge and tools necessary to overcome common obstacles. From setting up secure tunnels to configuring your Mac for optimal performance, we'll walk you through each step of the process. Along the way, we'll also highlight best practices, common pitfalls to avoid, and tips for troubleshooting. By the end of this guide, you'll have the confidence to remotely connect IoT devices behind firewalls on your Mac, all while maintaining the highest levels of security.
Read also:Pedro Martinez The Legend Who Redefined Pitching
Table of Contents
- What is Remote Connect IoT?
- How Does Firewall Affect IoT Connectivity?
- Why Choose Mac Over Windows for IoT?
- Can You Bypass Firewall on Mac Without Windows?
- Steps to Secure Remote IoT Connectivity
- What Are the Best Practices for IoT Security?
- Troubleshooting Common Issues
- FAQ Section
- Conclusion
What is Remote Connect IoT?
Remote Connect IoT refers to the ability to manage, monitor, and interact with IoT devices from a remote location. This concept has revolutionized industries ranging from healthcare to manufacturing by enabling real-time data collection and analysis. IoT devices, such as sensors, cameras, and smart appliances, rely on internet connectivity to function effectively. However, ensuring secure and reliable remote access is crucial, especially when dealing with sensitive data. In this section, we'll explore the fundamentals of IoT and why remote connectivity is essential for modern applications.
Key Benefits of Remote Connect IoT:
- Enhanced efficiency through real-time monitoring
- Reduced downtime due to quick troubleshooting
- Improved scalability for large-scale IoT deployments
For Mac users, achieving remote connectivity requires leveraging native tools and third-party applications that are compatible with macOS. Unlike Windows, macOS offers a Unix-based architecture that provides robust networking capabilities. By combining these features with secure protocols like SSH and SSL, users can establish a reliable connection to IoT devices behind firewalls.
How Does Firewall Affect IoT Connectivity?
Firewalls play a critical role in securing networks by blocking unauthorized access. However, they can also pose challenges for IoT devices that require external connectivity. Firewalls are designed to filter incoming and outgoing traffic based on predefined rules, which can inadvertently block legitimate IoT traffic. Understanding how firewalls affect IoT connectivity is essential for overcoming these obstacles.
Common Firewall Challenges:
- Blocking of specific ports required for IoT communication
- Restricting access to external IP addresses
- Interfering with secure tunneling protocols
By configuring firewalls to allow specific traffic, users can ensure that IoT devices remain accessible while maintaining network security. Techniques such as port forwarding, DMZ setup, and using secure tunnels can help bypass firewall restrictions. Additionally, implementing advanced firewall rules that prioritize IoT traffic can further enhance connectivity.
Read also:Ralph Lauren The Timeless Elegance Shaped By Celebrity Influence
Why Choose Mac Over Windows for IoT?
While Windows remains a popular choice for IoT applications, macOS offers several advantages that make it an attractive option for remote connectivity. One of the primary benefits is its Unix-based architecture, which provides robust networking capabilities and seamless integration with Unix-based servers. This makes it easier to configure secure connections and manage IoT devices.
Advantages of Using Mac for IoT:
- Native support for secure protocols like SSH and SSL
- Compatibility with Unix-based IoT platforms
- Enhanced security features built into macOS
Furthermore, macOS offers a user-friendly interface that simplifies the setup and management of IoT devices. With tools like Terminal and third-party applications, users can easily configure secure connections without the need for complex scripting. This makes macOS an ideal choice for both beginners and advanced users alike.
Can You Bypass Firewall on Mac Without Windows?
Bypassing a firewall on a Mac without relying on Windows is entirely possible, provided you have the right tools and knowledge. The key lies in leveraging secure tunneling protocols and configuring your Mac to work seamlessly with IoT devices. Techniques such as SSH tunneling, port forwarding, and using reverse proxies can help establish a secure connection while bypassing firewall restrictions.
Steps to Bypass Firewall on Mac:
- Configure SSH tunneling to create a secure connection
- Set up port forwarding rules on your router
- Use a reverse proxy to redirect traffic
By following these steps, users can ensure that their IoT devices remain accessible while maintaining network security. Additionally, implementing advanced firewall rules that prioritize IoT traffic can further enhance connectivity. It's important to note that bypassing firewalls should only be done with proper authorization and in compliance with network policies.
Steps to Secure Remote IoT Connectivity
Securing remote IoT connectivity involves a combination of best practices and advanced techniques. From configuring firewalls to implementing encryption protocols, users must take a holistic approach to ensure the highest levels of security. In this section, we'll outline the key steps required to achieve secure remote connectivity on a Mac.
Key Steps to Secure Remote IoT Connectivity:
- Configure firewalls to allow IoT traffic
- Implement encryption protocols like SSL and TLS
- Use secure tunneling protocols like SSH
By following these steps, users can ensure that their IoT devices remain secure while maintaining seamless connectivity. Additionally, regularly updating firmware and software can help protect against vulnerabilities and ensure optimal performance.
What Are the Best Practices for IoT Security?
IoT security is a critical concern for users and organizations alike. With the increasing number of connected devices, ensuring security has become more important than ever. Best practices for IoT security include implementing strong authentication mechanisms, regularly updating firmware, and monitoring network traffic for suspicious activity.
Best Practices for IoT Security:
- Use strong passwords and two-factor authentication
- Regularly update firmware and software
- Monitor network traffic for anomalies
By adhering to these best practices, users can significantly reduce the risk of security breaches and ensure the safe operation of their IoT devices.
Troubleshooting Common Issues
Despite careful planning and implementation, users may encounter issues when setting up remote IoT connectivity. Common problems include connectivity failures, firewall restrictions, and compatibility issues. In this section, we'll explore some of the most common issues and provide solutions to help users overcome them.
Common Issues and Solutions:
- Connectivity failures: Check network settings and ensure proper configuration
- Firewall restrictions: Configure firewall rules to allow IoT traffic
- Compatibility issues: Use compatible tools and applications
By addressing these issues promptly, users can ensure uninterrupted connectivity and optimal performance of their IoT devices.
FAQ Section
What is the easiest way to remotely connect IoT devices on a Mac?
The easiest way to remotely connect IoT devices on a Mac is by using SSH tunneling. This method provides a secure and reliable connection while bypassing firewall restrictions. Additionally, configuring port forwarding on your router can further enhance connectivity.
Can I use third-party applications for remote IoT connectivity on Mac?
Yes, third-party applications can be used to enhance remote IoT connectivity on a Mac. Tools like ngrok and tunnelbear offer user-friendly interfaces and advanced features that simplify the setup process. However, it's important to choose reputable applications and ensure they comply with security standards.
How often should I update my IoT device firmware?
It's recommended to update IoT device firmware regularly, ideally every few months or whenever a new update is available. This ensures that your devices remain secure and compatible with the latest technologies.
Conclusion
In conclusion, achieving secure remote connect IoT behind firewall on a Mac without Windows is entirely possible with the right tools and knowledge. By leveraging advanced networking techniques and secure protocols, users can ensure seamless connectivity while maintaining robust security measures. Whether you're managing home automation systems or industrial IoT applications, this guide provides the insights and tools necessary to succeed. Remember to follow best practices, address common issues promptly, and regularly update your devices to ensure optimal performance and security.
With the growing importance of IoT in modern society, the ability to remotely connect devices behind firewalls on a Mac is becoming increasingly valuable. By embracing these technologies and techniques, users can unlock the full potential of IoT and transform the way they interact with technology.
Meta Description: Learn how to achieve secure remote connect IoT behind firewall mac download without windows. Discover advanced techniques, best practices, and troubleshooting tips for seamless connectivity.